In today’s interconnected world, small businesses find themselves navigating an ever-evolving digital landscape filled with both possibility and risk. While technology opens doors to innovation and growth, it also invites cyber threats that can disrupt operations, compromise sensitive facts, and drain valuable resources.For small business owners,cybersecurity isn’t just a technical concern—it’s a critical component of protecting their livelihood. This article delves into practical, approachable cybersecurity tips designed to empower small business owners to build a robust defense, safeguard their assets, and confidently embrace the digital age.
Understanding the Cyber Threat Landscape for Small Businesses
Small businesses today find themselves navigating an increasingly complex digital surroundings, where cyber threats evolve with alarming speed.Unlike large enterprises, which ofen have dedicated cybersecurity teams, small businesses must adopt a proactive stance to defend against attacks like phishing scams, ransomware, and data breaches. The reality is that cybercriminals target smaller companies precisely because they assume they are less protected, making it crucial to understand that no business is too small to be a target.
Key vulnerabilities frequently enough stem from limited IT resources and insufficient employee training, creating gaps hackers are eager to exploit. Business owners should prioritize safeguarding sensitive data, from financial information to customer records, by implementing multi-layered security measures. This includes:
- Regular software updates: Ensures security patches are applied promptly.
- Strong password policies: Enforces complexity and frequent changes.
- Employee education: Builds awareness of phishing and social engineering tactics.
To illustrate how different threats vary in impact, consider the following simplified risk assessment table:
| Threat type | Potential Impact | detection Complexity |
|---|---|---|
| Phishing | Data theft, financial loss | Low |
| Ransomware | System lockdown, business disruption | Medium |
| Insider Threats | Data leaks, reputation damage | High |
Understanding these risks empowers small business owners to allocate resources wisely and partner with trusted cybersecurity providers. For in-depth guidelines and tools,authoritative organizations like the Cybersecurity and Infrastructure Security Agency (CISA) and Federal Trade Commission (FTC) offer invaluable resources tailored to small business needs.

Building a Strong Password Strategy That Works
Creating passwords that are both secure and memorable is a balancing act, but it’s essential to protect your small business from cyber threats.Instead of relying on common words or easily guessed phrases,focus on developing a passphrase — a combination of random words linked together — or use a password manager to generate complex unique passwords for every account.This reduces the risk of credential stuffing attacks, where hackers reuse stolen passwords across multiple sites.
To strengthen your defense even further, incorporate these key elements into your password strategy:
- Length over complexity: Aim for passwords with at least 12 characters—longer passwords are harder to crack than short ones with special characters.
- Uniqueness: Never reuse passwords across different platforms or services.
- two-factor authentication (2FA): Add an extra layer of security by using apps like Authy or google Authenticator.
| Password Type | Example | Security Score |
|---|---|---|
| Simple word | Sunshine123 | Low |
| Complex mixed characters | G7!sDf$9kP | Medium |
| Long passphrase | BluePineapple_CoffeeTrip7! | High |
By adopting these practices,you’ll not only defend your business data more effectively but also stay ahead of evolving cyberattack methods. For more detailed guidance on password management, visit the Cybersecurity and Infrastructure Security Agency.

Implementing Multi-Factor authentication Across Your Systems
Strengthening your business’s security doesn’t have to be complicated. One of the most effective measures to safeguard your digital assets is by layering your login processes. Instead of relying solely on passwords—which can be weak or compromised—incorporating additional verification steps ensures only authorized users gain access. This multi-layered defense greatly reduces the risk of unauthorized breaches.
Start by integrating authentication methods that blend knowledge, possession, and biometric factors. Examples include:
- Time-sensitive codes sent to your mobile device via SMS or authenticator apps like Authy or Google Authenticator
- Physical security keys using USB or NFC standards, such as FIDO2 certified devices
- Biometrics, like fingerprint scans or facial recognition, integrated via modern hardware
| Factor Type | Example Methods | Security benefits |
|---|---|---|
| Knowledge | Password, PIN | Easy to implement but vulnerable if weak or reused |
| Possession | SMS code, hardware token | Requires physical device, adds strong security layer |
| Inherence | Fingerprint, facial ID | Unique to user, difficult to imitate or steal |
When rolling out this enhanced security, keep user experience in mind to avoid frustration—opt for options that balance convenience with protection. For detailed insights on implementing robust MFA solutions, the Cybersecurity and Infrastructure Security Agency offers excellent guidelines tailored to businesses of all sizes.
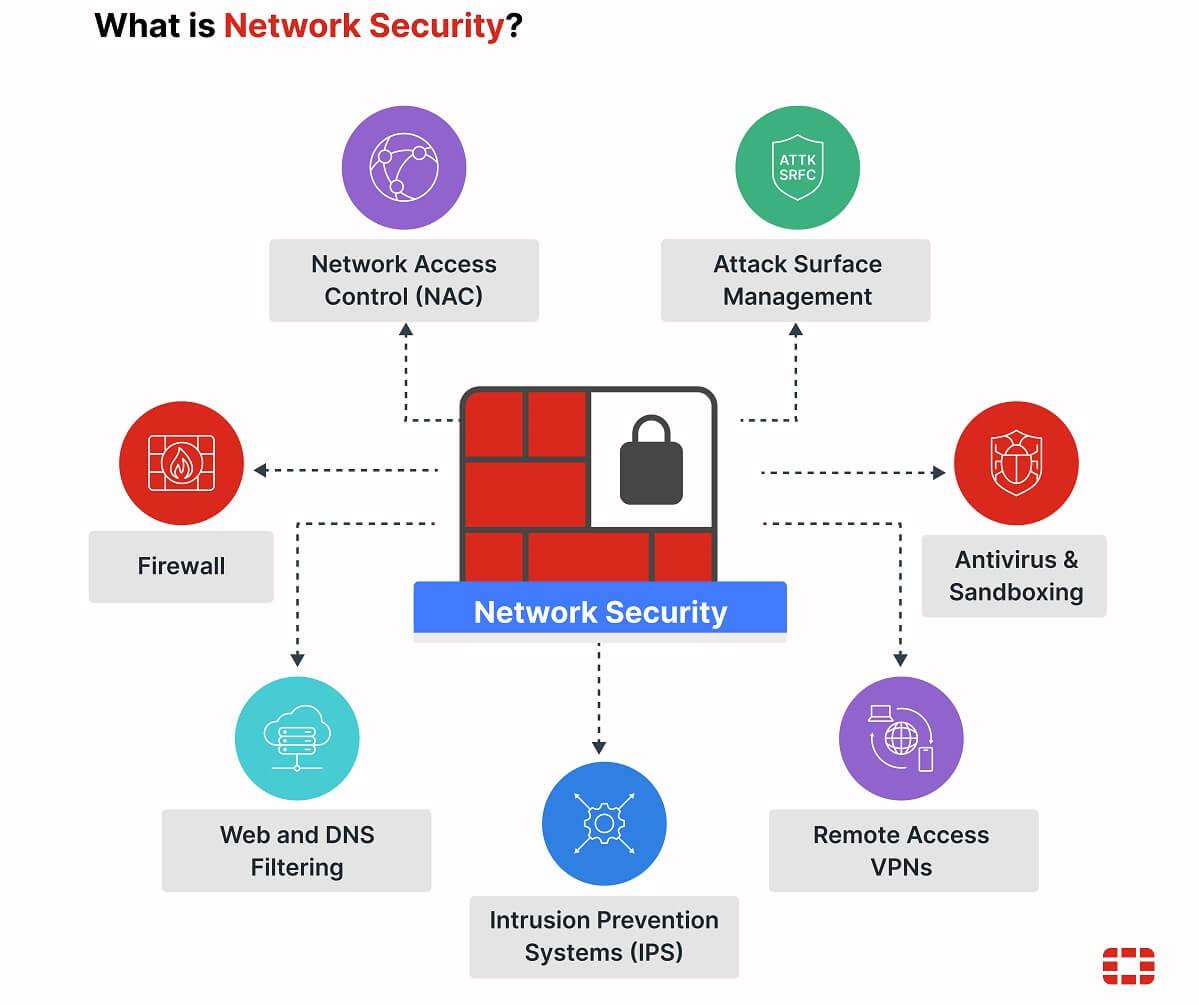
Securing Your Network and Cloud Services Effectively
Protecting your digital assets starts with a robust network and cloud security strategy tailored for small business needs. First, implement a strong perimeter defense by setting up firewalls and intrusion detection systems. Ensure your Wi-Fi network is encrypted with WPA3 standards and segment guest access to limit exposure. Regularly update firmware and security patches to close vulnerabilities that cybercriminals often exploit.
Cloud services require an equally vigilant approach. Choose providers that offer end-to-end encryption and comply with industry standards such as ISO 27001. Use multi-factor authentication (MFA) to secure user access and consistently review access permissions to avoid needless exposure. Backup critical data periodically and verify that your recovery plan is tested and accessible. For additional insights, explore authoritative resources like the Center for Internet Security and NIST.
| Security Measure | Benefit | Advice |
|---|---|---|
| Firewall | Blocks unauthorized network access | Enable with strict rules |
| Multi-Factor Authentication | Prevents unauthorized logins | Use for all cloud services |
| Regular Backups | Ensures data recovery after incidents | Automate and test frequently enough |
- Monitor logs: Analyze network and cloud activity to detect suspicious patterns early.
- Use VPNs: Encrypt connections when accessing your network remotely.
- Educate staff: Conduct regular training on recognising phishing attempts and safe practices.

Creating a Cybersecurity Awareness culture Within Your Team
Building a team that actively prioritizes cybersecurity starts with education and engagement. Empower your employees by offering regular, interactive training sessions that cover everything from recognizing phishing attempts to best password practices. Emphasize how their individual actions contribute to the company’s overall security posture, turning a potentially dry topic into a shared mission. Encourage questions and foster an environment where team members feel cozy reporting suspicious activity without fear of blame.
- Personalize training: Tailor cybersecurity lessons to specific roles for maximum relevance.
- Use real-world examples: Share recent cyberattack stories that resonate with your industry.
- Promote strong password hygiene: Implement password managers and multi-factor authentication.
- Celebrate wins: Recognize employees who adhere to best practices to reinforce positive behaviors.
| Cybersecurity Practice | Team Benefit | Implementation Tip |
|---|---|---|
| Phishing Awareness | Reduced successful attacks | Simulated phishing tests monthly |
| Regular Updates | Strong defense against exploits | Automate software patches |
| Incident Reporting | Rapid containment | Clear reporting channels |
for further guidance on cultivating a cybersecurity-conscious workplace, resources offered by CISA and NIST Cybersecurity Framework provide excellent best practices and training frameworks.
To Wrap It Up
In the ever-evolving digital landscape, safeguarding your small business is not just a necessity—it’s a commitment to resilience and trust. By weaving these cybersecurity tips into your daily operations, you build more than just defenses; you create a foundation for growth and confidence in the face of uncertainty.Remember, cybersecurity isn’t a destination but a journey—one that evolves with your business. Stay vigilant, stay informed, and let your vigilance be the shield that keeps your entrepreneurial dreams secure.